DDoS Attacks are on the rise, and every Website and Server online is a potential target. These attacks can bring down websites, disrupt services, and cause significant financial losses This is why why DDoS protection is essential to stay ahead of these growing threats.
A DDoS Attack is an attempt to make a Web Server or Website unavailable or to go down by overwhelming it with traffic from numerous sources. The attacks will target a broad range of websites from banks and news sites and target small businesses, individual websites, political platforms. No Website or Web Server is immune to DDoS Attacks.
DDoS attacks can have a damaging consequence on a businesses bottom line, both with mitigation costs and lost revenue. The attacks result in lasting damage to the reputation of a company and could hurt customer loyalty.
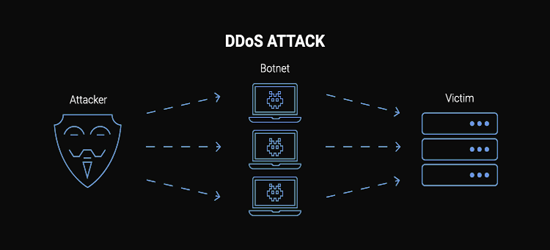
Attackers create a network of infected machines called botnets. This is done by spreading malicious software through Websites, Social Media, and even emails. They can then manipulate these machines without your knowledge or consent and even use these machines as an army to launch an attack against the targeted Website or Web Server. Some botnets can be hundreds or thousands of computers linked in an attack. An unprotected website stands almost no chance.
Botnets can produce massive floods of traffic to overwhelm a Server. The floods can be produced in a large range of different ways, which can include sending vast amounts of random data to consume the target's bandwidth.
Unfortunately, almost anyone can get their hands on DDoS For Hire Services through underground markets to disrupt a company’s online operations.

When a website or online service is inundated with malicious traffic (DDOS attacks), it can experience significant disruption, leading to loss of availability and severe consequences for business operations. This disruption often results in immediate financial losses due to interrupted services or sales, and can cause long-term reputational damage as users and customers lose trust in the affected entity's reliability. Additionally, the financial burden of mitigating the attack and recovering systems can be substantial, encompassing costs for technical resources, legal fees, and compliance-related expenses. In extreme cases, persistent DDoS attacks can lead to regulatory penalties if they breach service level agreements or industry regulations, compounding the overall impact on the organization's financial health and public image.
The consequences of a successful DDoS attack can be severe, including:
The most common symptom of a DDoS attack is when a website, Server, or services suddenly becoming slow or unavailable.
Keep in mind that a number of causes, such a legitimate spike in traffic, can create similar performance issues. Traffic analytics tools can help you spot some signs of a DDoS attack.
There are other, more specific signs of attacks that can vary depending on the type of DDOS attack.

DDoS Application Layer Attacks are sophisticated Cyber Threats designed to disrupt services by overwhelming the application layer, where user interactions occur. They fill the botnets with a complex request that overwhelms the target Server. And If the target Web Server receives thousands or millions of requests, it can be overwhelmed and either slow down or stop completely. Unlike traditional DDoS attacks that flood networks, these target specific application processes, such as HTTP, DNS, or database queries, simulating legitimate user behavior. By inundating servers with resource-intensive requests, attackers exhaust system capabilities, slowing or crashing services entirely. These attacks are stealthy, often harder to detect, and can cripple business-critical applications. Effective defense requires advanced traffic analysis, robust security protocols, and scalable infrastructure to distinguish malicious activity from genuine user interactions and maintain seamless service availability.
This type of attack is focused on the networking layer of the target Web Server or Website. Its focus is to overwhelm the table space at the firewall, central network services or load balancer that sends requests to the target. Generally, network service follows the first in first out (FIFO) command, where the Server processes the first request before it goes to the next one. In a DDoS Attack, the queue can become so large that the Server lacks the resources to handle the first request.
The botnet is used to generate a large amount of traffic and block the works on the target – more of like an HTTP Flood attack, but with more exponential response component. Think of 50 orders coming in for 20 items each at the same store at the same exact time. When such an attack is directed to a Web Server, it will increase the response size, and the traffic amount explodes and clogs up the target.
Rate limiting restricts the volume of network traffic over a specific time period, essentially preventing Servers from getting overwhelmed by requests from IP addresses. Rate limiting can be used to prevent DDoS attacks that use botnets to spam an endpoint with an abnormal amount of requests at once. It is a strategy for managing and regulating traffic flow to ensure that the service remains available and responsive.
DDoS attacks can have severe consequences for businesses and organizations:

In February 2018, there was the first-ever terabit-size DDoS attack. This was followed days later by an attack nearly twice that big, measuring 1.7 Tbps. (terabits per second).
Not only are more DDoS Attacks being launched today, but the attackers are also uncovering new ways to integrate the latest technologies for large scale attacks. In 2019, the attacks inclined towards big volumes and large websites, but in 2021 we have seen the highest level of attack ever recorded. And this is not about to slow down.
Attackers are starting to combine the attacks with other expensive illegal activity that can raise the recovery cost to include compulsory customer notification, breach reporting, and more complex recovery.
DDoS Attacks are increasingly multilayered and multivector, using a blend of massive volume attacks and stealth infiltration. This is the newest trend in an evolving landscape where perpetrators adapt their services and utilize advanced tools and abilities to try to evade and overcome existing defenses. Organizations need to maintain a consistent vigilance on the methods used to target their systems and constantly adjust their defenses as per the industry standards to stay safe.
A good hosting provider should have staff that is experienced in stopping DDoS attacks. In the event that you identified symptoms of a DDoS attack, contact your hosting provider and ask for their help. Depending on the Provider, they might have detected and stopped it before doing any harm.
But for any organization, the best solution is to plan ahead for a DDoS attack. Using a “Always On” type of protection or clear protocols in place for your business to follow when the attack occurs.
For example, instead of stopping all traffic, you might continue to allow users to use the website as much as you can. You could also switch to a different system to work from.
Businesses that are vulnerable to attacks on mobile devices should make sure that private devices connected to the corporate network have an approved mobile security solution to protect against infections. And the means to prevent installation of unauthorized apps. Your IT department should be vigilant in sniffing out and intercepting any malicious communications.
If it is absolutely necessary to share login information, make sure that it is sent via encrypted channels.

Educating your team about DDoS attacks is crucial for ensuring a swift and effective response to these disruptive threats. Providing comprehensive training helps team members recognize the early signs of a DDoS attack, understand the appropriate response procedures, and implement preventative measures. By fostering a culture of awareness, you empower your staff to quickly identify anomalies in traffic patterns, coordinate with IT and security professionals, and execute predefined incident response plans. Regular training sessions and simulations not only keep the team informed about the latest attack techniques and mitigation strategies but also enhance their ability to act decisively under pressure. This proactive approach minimizes the potential impact of DDoS attacks and strengthens the overall resilience of your organization's digital infrastructure. Ensure that your team understands:
Despite best efforts, some attacks may still succeed. Having a response plan is crucial to minimize damage:
As DDoS attacks become more sophisticated, integrating artificial intelligence (AI) into mitigation strategies has revolutionized website protection. AI-driven systems analyze traffic patterns in real-time, distinguishing legitimate users from malicious botnets with high precision. By predicting attack behaviors and dynamically applying rate limits, these solutions effectively counter even subtle, short-lived attacks that traditional defenses might miss.
AI-powered DDoS protection ensures robust security, maintaining website uptime and safeguarding brand reputation against evolving cyber threats.

Modern DDoS protection relies on advanced tools and technologies. Here are some of the top options:
Adopting preventive measures against DDOS attacks is as important as having a response plan. Here are some best practices:

For WordPress users, integrating robust security plugins can significantly bolster defenses against DDoS attacks and other cyber threats. These plugins, often available in free and premium versions, integrate seamlessly with our WordPress hosting accounts, offering WordPress users an accessible, layered approach to safeguarding their websites from downtime and data breaches caused by DDoS attacks and other vulnerabilities
Defender Security is a powerful WordPress plugin offering malware scanning, firewall protection, and Two-Factor Authentication. It blocks brute-force attacks, monitors file changes, and provides easy security tweaks to keep your site safe and optimized.
The Anti-Malware Security and Brute-Force Firewall plugin by GOTMLS.NET is a powerful WordPress tool that scans for malware, viruses, and vulnerabilities, offering automatic removal of known threats and robust protection against brute-force attacks.
Stop User Enumeration is a lightweight WordPress plugin that enhances security by blocking malicious bots and hackers from scanning your site for user login details. It prevents user enumeration attacks, protecting your site from unauthorized access and brute-force attempts.
Wordfence Security is a leading WordPress plugin offering a robust firewall, malware scanning, and live traffic monitoring. It blocks malicious IPs, prevents brute-force attacks, and ensures real-time protection, keeping your site safe from evolving cyber threats.
Security & Malware Scan by CleanTalk is a robust WordPress plugin offering a real-time firewall, malware scanner, and brute-force protection. It logs security events, blocks suspicious IPs, and ensures your site stays safe from hacks and vulnerabilities.
All-In-One WP Security & Firewall is a comprehensive WordPress plugin that strengthens site security with a user-friendly firewall, brute-force protection, and malware scanning. It blocks malicious login attempts and enhances database safety effortlessly.
Security Ninja is a trusted WordPress plugin since 2011, delivering 50+ security tests, malware scans, and a firewall. It blocks brute-force attacks, monitors vulnerabilities, and offers one-click fixes, ensuring robust protection without slowing your site.
Rate Limit Guard is a WordPress plugin designed to shield sites from DDoS and brute-force attacks. It uses smart rate-limiting to block excessive requests from IP stressers and bots, ensuring resource efficiency and uptime with easy setup.
Anti-Hacker is a robust WordPress plugin that fortifies your site against hackers with a firewall, malware scanner, and brute-force protection. It hides sensitive data, disables XML-RPC, and blocks malicious IPs, ensuring comprehensive security.
Astra Security Suite is a top-tier WordPress plugin with a real-time firewall, AI-powered malware scanner, and brute-force protection. It secures sites against 100+ threats, offers instant cleanup, and installs in minutes, no DNS changes needed.
DDoS attacks are an ongoing threat to an organization’s security. Modern security technologies have developed mechanisms to defend against most forms of DoS attacks. Stay vigilant, continuously assess your security measures, and leverage reliable DDoS protection solutions to ensure the resilience of your infrastructure.
By implementing the protection and prevention strategies outlined above, you’ll not only safeguard your digital assets but also build trust with your users by demonstrating a commitment to security. Stay proactive, stay secure, and keep your website online, no matter the challenges.
A seasoned writer with over a decade of experience in major organizations and agencies. His portfolio...
This policy contains information about your privacy. By posting, you are declaring that you understand this policy:
This policy is subject to change at any time and without notice.
These terms and conditions contain rules about posting comments. By submitting a comment, you are declaring that you agree with these rules:
Failure to comply with these rules may result in being banned from submitting further comments.
These terms and conditions are subject to change at any time and without notice.
Tweet Share Pin Email.
Comments (1)
Thanks for the detailed breakdown on DDoS protection strategies! I run a small e-commerce site and have been worried about potential attacks after hearing about recent incidents. Your article mentions AI-driven systems for real-time traffic analysis. Do you recommend any specific tools or services for a small business like mine to implement this? Also, how effective are plugins like Rate Limit Guard for WordPress in preventing these attacks? Appreciate the insights